Security Advisory
QR Code Phishing
Description
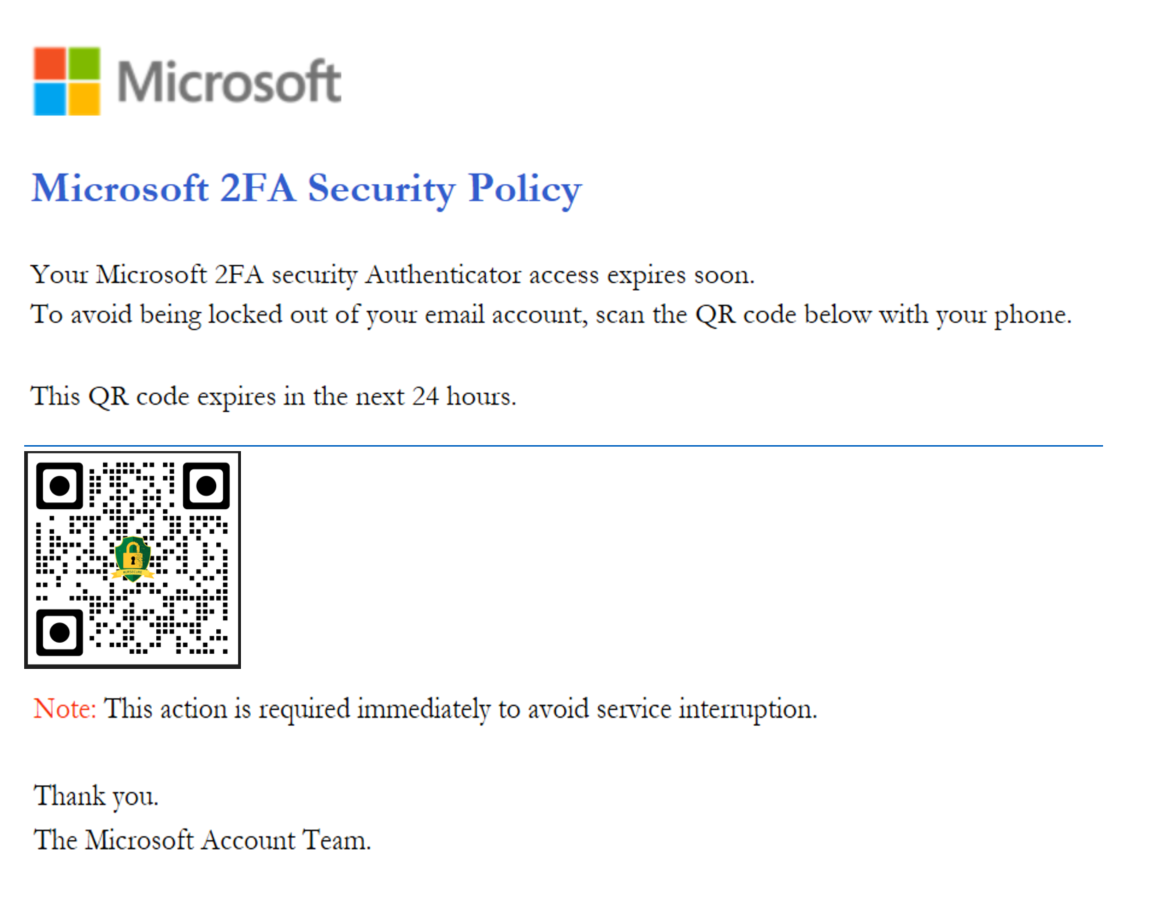
The University has been receiving QR Code Phishing attempts. This attack uses a technique referred to as ‘Quishing’. The observed activity consists of actors sending malicious links embedded in QR Codes attached to legitimate looking emails claiming to be from trusted sources. For example, we have seen malicious emails masquerading as Microsoft 2FA security requests.
When the malicious QR Code is scanned by a device, it will lead potential victims to a legitimate looking, yet malicious website requesting the employee’s username and password, most commonly for their Microsoft account. These malicious emails create a false sense of urgency to encourage users to submit their credentials quickly, potentially enabling malicious actors to perform further actions such as data theft, system damage, or unauthorized access to your device.
Example Email:
From: "Uregina |Support" <Unknown@BadGuy.net>To: Regina.User@uregina.ca
Subject: Authentication Required For URegina User
Impact
- This style of phishing attack can be successful because it's often mistaken for a legitimate email.
Resolution
- The email can be reported to report.phishing@uregina.ca and deleted.
- If you receive a phishing email or are uncertain about the legitimacy of an email message, please forward the email message as an attachment to the report.phishing@uregina.ca.
If you are concerned about the security of your account after receiving a phishing message, you can take the following actions:
- Change your password. https://app2.uregina.ca/perl/chpass.pl
- Choose a password that is:
- Completely different than your previous password.
- Not used anywhere else.
- Does not contain your previous password.
- Check your account for email forwarding and mailbox rules.
Resources
- Take cyber security awareness training available to all faculty and staff on Beauceron - https://www.uregina.ca/is/security/training/training-register.html